Almost everyone believes that when it comes to Internet Security once antivirus software is installed all is good; this is a huge misconception that many antivirus software vendors would like you to believe! That if you buy their top of the line software suites and all is safe (NOT TRUE).
Threats and infections can come from the most unexpected places. One example my daughter’s Nintendo DS had become my dogs chew toy, so my wife typed into Google “DS Repair†and clicked on the returned search result; next thing that happened was her computer was infected with a virus resulting in a complete restore of her operating system.
You should still install Anti-Virus software (read my recommendations on free antivirus software.)
First Recommendation: Always keep antivirus software definitions up to date.
Always scan every foreign file brought into your system: all downloads, attachments, and files from USB drives. To do this, save the file then right click on it and select “scan file withâ€. I personally scan everything, even if I know the person whose file it is; better to be safe than sorry!
Along with your Antivirus software, you should keep your Operating System and Browser Software up to date. Security holes are constantly being exploited and patches are constantly being distributed: Stay Updated!!!
Never load a program in which you are not aware of its manufacturer or purpose, question yourself if you need this program; if you believe you do need the software, always create a restore point before install. Do your research on the program, does the program have a valid digital signature or any bad reviews?
Second Recommendation: Stay out of the red light district of porn. More times than not, I will be asked to recover a computer from various types of attacks primarily because they stray into the red light district of porn sites.
Third Recommendation: Downloading either pirated software or other types of copyrighted material, you can eventually expect to be infected. Nothing is free my friends. Don’t get me wrong torrent sites and file sharing can be very useful, providing a wealth of useful and legitimate material. Tread lightly and again always scan your downloads!
Forth Recommendation:Â Always Backup regularly! With Windows 7, you can use the built-in backup program to save an image backup on an external hard drive or media. With a Mac can also create the same type of backup routine using Mac’s Time Machine. Â Â Also, it is good investment to purchase an external hard drive. Most now come with very simple backup programs and their prices have dropped considerably. A few well reviewed recommendations.
Seagate Storage Solutions
Seagate Storage Solutions: Seagate Home
Seagate Portable Drives:Â Seagate Portable Drives
Seagate FreeAgent GoFlex Ultra-Portable Drive (500GB)
FreeAgent® GoFlex™ Ultra–portable Drive
This ultra–upgradable, ultra–portable hard drive makes it ultra–easy for you to store, backup, encrypt and access your files anytime, anywhere.
- Features USB 2.0 or 3.0 plug–and–play connectivity
- Includes pre–loaded easy–to–use backup software
- Lets you upgrade to USB 3.0, FireWire® 800 or eSATA
- Allows you to access your content on your TV, network and on–the–go when combined with other GoFlex devices
Western Digital
Western Digital: Western Digital
Western Digital External Drives:Â Western Digital External Drives
Western Digital My Passport Essential SE
WD quality inside and out.
My Passport portable drives are the world’s best selling drives. There’s a reason. We’ve been making hard drives for 20 years and we know how to protect your data.
USB 3.0 plus USB 2.0.
A single drive with universal compatibility today and next-generation speed for tomorrow. Use it with USB 2.0 now and step up to USB 3.0 speed when you’re ready. High capacity in a smaller drive. Massive capacity in this small, stylish drive that is powered directly from the USB port on your PC. No separate power supply is needed. You can enjoy the movies, music and photos you store on this drive on your TV?
Verbatim Storage Solutions
Verba tim Storage Solutions: Verbatim Home Page
tim Storage Solutions: Verbatim Home Page
Verbatim Portable Drives: Verbatim Portable Drives
Verbatim Store’n'Go SuperSpeed USB 3.0 (500GB)
Experience transfer speeds up to 10x faster with the new SuperSpeed USB 3.0! This Verbatim compact external portable hard drive features a sleek piano-black finish and comes with the fastest USB connectivity available. SuperSpeed USB 3.0 lets you blaze through demanding tasks by reading and saving files faster. This external hard drive features Nero BackItUp & Burn Essentials software that allows full system backup and restore functions, the ability to schedule automatic backup by date/time and an encrypted backup option with password control. Save your precious photos, videos, graphics, games, music, data and more in ultimate safety with Verbatim.
- Compact, portable drive features a sleek piano black finish
- SuperSpeed USB 3.0 increases transfer speed up to 10x faster than USB 2.0
- Backwardly compatible with USB 2.0 ports
- Includes Nero BackItUp & Burn software*
- Bonus Norton Online Backup (5GB) free trial
- Industry-leading 7-year limited warranty
*Software compatible with Windows operating systems only
Fifth Recommendation: Spam You should never trust the sender of an e-mail if you do not know the sender or did not request the information or ask to be put on their mailing list. Spam filtering services are a very effective and do a good job reducing Spam by having it bypass your inbox. The spam filters can be taught and adapt to changing threats. Depending on the spam filter you use, the better chance you won’t receive fraudulent emails. Spam is the primary delivery methods of malware, financial scams and phishing attacks.
“Spam is the use of  email systems (including most broadcast media, digital delivery systems) to send unsolicited bulk messages indiscriminately. While the most widely recognized form of spam is e-mail spam, the term is applied to similar abuses in other media: instant messaging spam, Usenet newsgroup spam, Web search engine spam, spam in blogs, wiki spam, online classified ads spam, mobile phone messaging spam, Internet forum spam, junk fax transmissions, social networking spam, television advertising and file sharing network spam.
Spamming remains economically viable because advertisers have no operating costs beyond the management of their mailing lists”
Spam Filtering Software
Cactus Spam Filter (Free)
SpamAssassin
Spy Sweeper 2011
Sixth Recommendation: Don’t lose your cool or panic. Don’t do anything drastic until you know what threat you’re dealing with. Don’t be afraid to contact someone for assistance (friend or family). Don’t purchase any tools (pop ups) that are advertised by your threat; you can tell it is a threat if you click the “x†and the pop up will not close and is persistent. Any threat that gets you to purchase their software is not a legitimate software vendor. Most of the time they hijack your computer and want you to purchase your own documents back!
Seventh Recommendation: NEVER, EVER provide passwords to anyone. NEVER, EVER provide your financial information to any un-trusted sources. If your uncertain it’s better to call with your financial purchase. A Little Common sense goes along way!
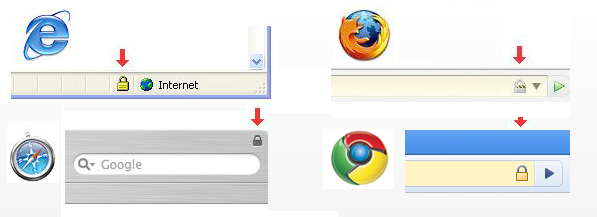
All current browsers have indicators or visual icons within the address bar whether you are in a trusted area or a secure connection. SSL Â “Secure Sockets Layer (SSL), are cryptographic protocols that provide communication security over the Internet TLS and SSL encrypt the segments of network connections above the Transport Layer, using asymmetric cryptography for privacy and a keyed message authentication code for message reliability, providing SSL”
If you found this article helpful share it with your friends on Facebook ![]() , twitter or email! Thanks!
, twitter or email! Thanks!







(248) 583-0125